Cyber security update
Over the past few years there has been a sharp rise in cyber attacks and scams.
They include well-publicised breaches against major corporations, including Sony, Kmart, US Postal Service and JP Morgan, and a host of celebrity data leaks. The attacks are not only on high-profile companies but any businesses or individuals that criminals can exploit.
Some security experts say spammers are winning the war and it’s not a matter of IF but WHEN your company will be infected.
Over the past few years there has been a sharp rise in cyber attacks and scams.
They include well-publicised breaches against major corporations, including Sony, Kmart, US Postal Service and JP Morgan, and a host of celebrity data leaks. The attacks are not only on high-profile companies but any businesses or individuals that criminals can exploit.
Some security experts say spammers are winning the war and it’s not a matter of IF but WHEN your company will be infected.
Ransomware
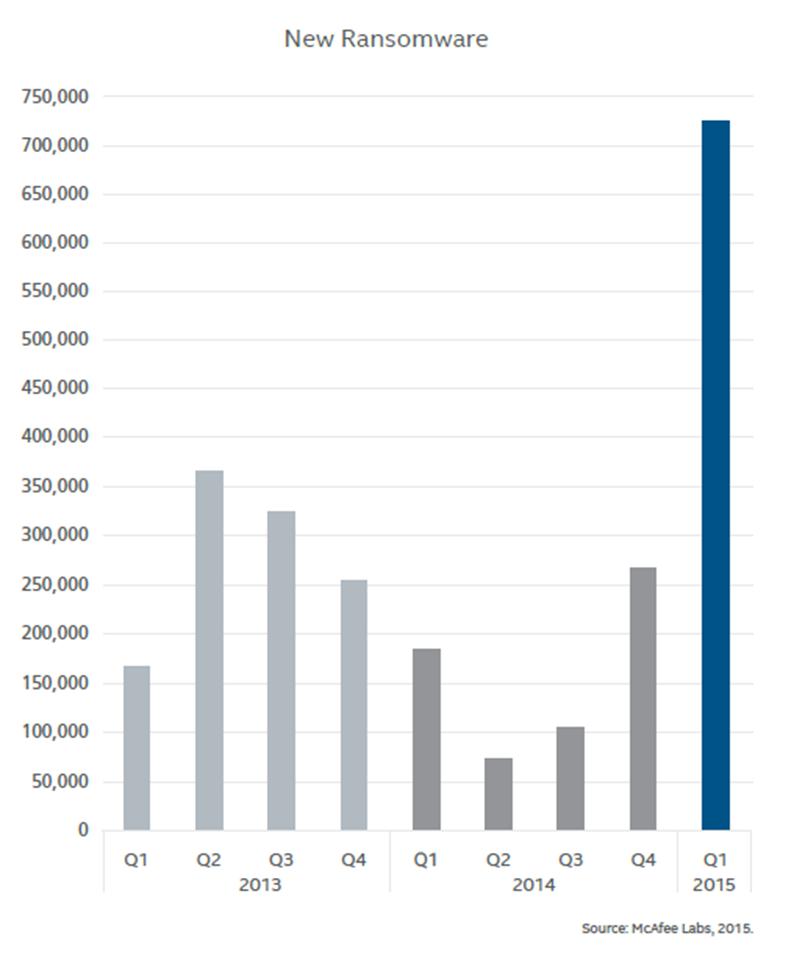
The current common threat is a ransomware virus called CryptoLocker. It encrypts user files on your computer and network drives and then prompts you for payment before the files are released. The virus propagates through HTML links within emails.
Clicking on a link downloads the virus, which starts automatically. The email hyperlinks usually come from seemingly official sources, such as the Australian Federal Police, the ATO, the RTA, and Australia Post. They are typically written in a way that causes an emotional response, such as receiving a speeding ticket, in the hope you will click the link without thinking.
What can you do?
First level requirements – this is a given for all businesses
1. Renew and update your multi-level security platform, as recommended by your IT partners
2. Maintain good Windows patching policies on servers and workstations
3. Ensure your website and web services all use SSL encryption and HTTPS
4. Introduce a password policy across the business
5. Ensure you have network folder-level security
6. Have proper backups
7. Educate your staff on the risks of opening unsolicited emails or not browsing the internet carefully
Second level requirements – these vary from business to business
1. Have your security policies and rules checked at least annually
2. Organise a vulnerability scan and external penetration test
3. If you keep any personal or credit card information, organise a PCI compliance scan
4. Develop a breach notification plan
5. Develop disaster recovery and business continuity plans
6. Buy a LAUW cyber insurance policy
News Alert August 2015
